SHIFTING PERSPECTIVE
SECURITY IS NOT A PRODUCT, IT IS A PROCESS
In today's ever-evolving digital landscape, the importance of cybersecurity cannot be overstated. Organizations and individuals must proactively safeguard their digital assets, sensitive information, and online presence.
However, a common misconception persists that we can achieve security simply by purchasing a product or implementing a one-time solution.
In this newsletter, we will explore the notion that security is not a product but rather an ongoing and dynamic process that requires continuous vigilance, adaptation, and collaboration.
PRODUCTS AND TOOLS LIMITATION
A sophisticated firewall, antivirus software, or the latest encryption protocol can single-handedly shield us from cyber threats. However, the reality is that even the most advanced tools can't guarantee complete protection. Hackers are continually evolving their tactics, and the digital landscape is constantly changing and evolving.
A security approach solely based on products and tools can leave gaps that attackers can exploit.
A sophisticated firewall, antivirus software, or the latest encryption protocol can single-handedly shield us from cyber threats. However, the reality is that even the most advanced tools can't guarantee complete protection. Hackers are continually evolving their tactics, and the digital landscape is constantly changing and evolving.
A security approach solely based on products and tools can leave gaps that attackers can exploit.
PROACTIVE THINKING
A security mindset involves proactive thinking, wherein individuals and organizations anticipate potential risks and vulnerabilities before we e. This mindset prompts regular risk assessments, scenario planning, and the implementation of measures to mitigate emerging threats.
CULTURE OF SECURITY
Cultivating a culture of security involves fostering an environment where everyone understands their role in protecting sensitive information. Employees should receive education about best practices, and safety becomes a shared responsibility rather than something left solely to the IT department.
CONTINUOUS LEARNING
Cyber threats continuously evolve, and a security mindset recognizes the importance of staying informed. Regular training and keeping up with the latest trends in cybersecurity ensure that defenses remain up-to-date and relevant.
ADAPTABILITY & FLEXIBILITY
COLLABORATION & COMMUNICATION
A security mindset emphasizes adaptability rather than relying on static measures. This statement means being prepared to pivot strategies, update protocols, and leverage emerging technologies to address novel threats.
A vital aspect of the security mindset recognizes that security is a collective effort. Collaboration with peers, sharing threat intelligence, and learning from others' experiences can bolster the overall security posture.
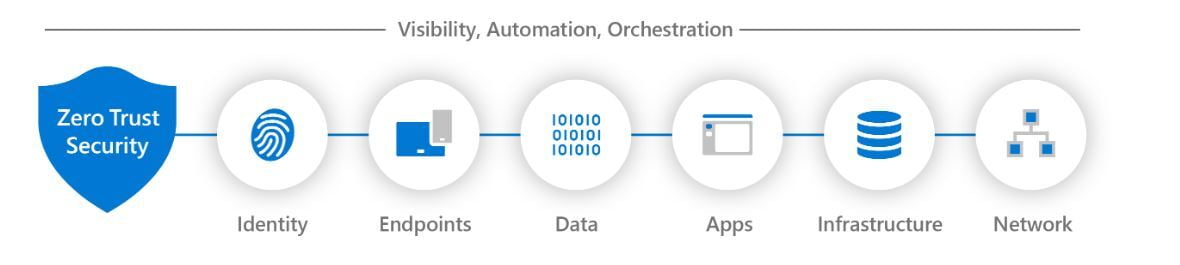
The Zero-Trust Approach : The road to success
The Zero Trust Approach is a well-known security strategy. It perfectly illustrates the sentence Security is not a product but a process. In fact, security relies on three pillars:
PEOPLE - PROCESSES - TECHNOLOGIES
This alliance is the winning combo for a proper defense strategy. All three are necessary for the overall balance. While advanced technologies surely provide the best defense tools and mechanisms, you still need adequate processes to deploy them and knowledgeable individuals to execute those.
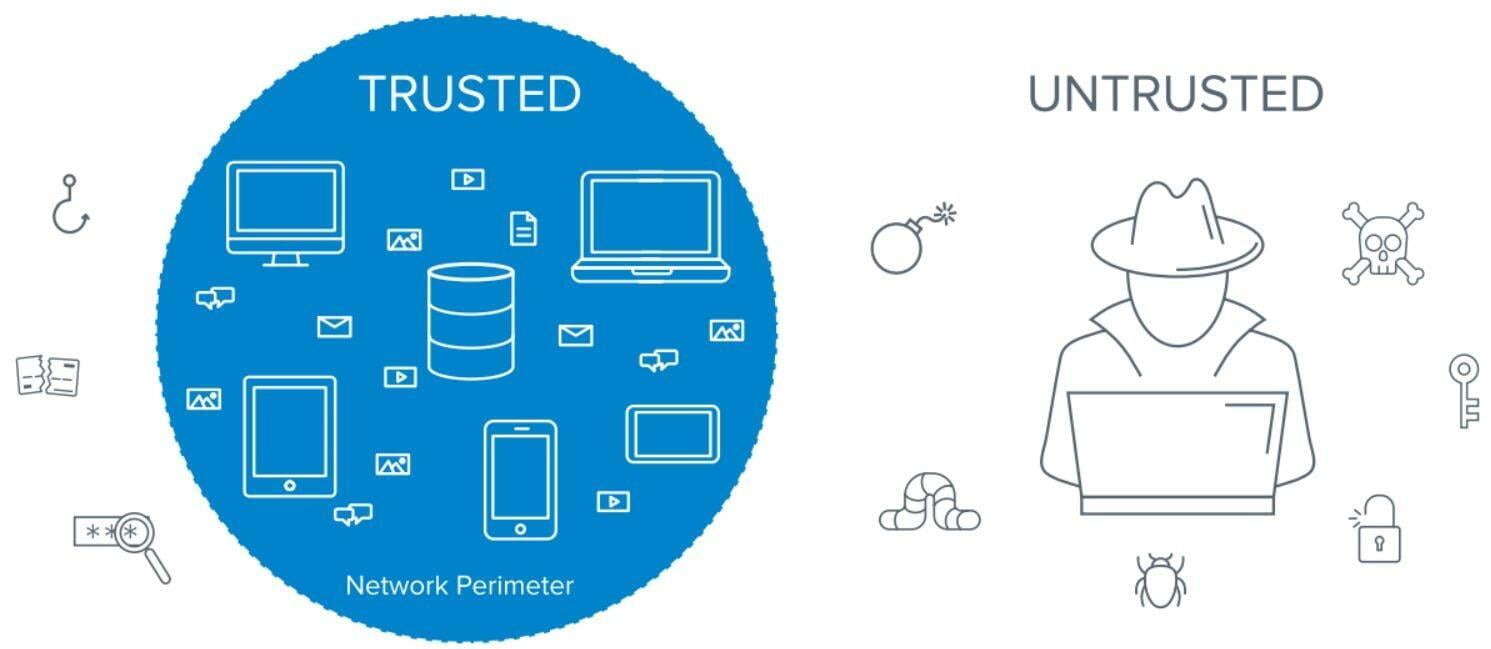
Zero Trust relies on assuming breaches rather than assuming safety. Instead of depending on traditional security products, it takes security breaches and treats every request made as unauthorized. Never trust; always verify is the idea.
IMPLEMENTING THE SECURITY MINDSET
EDUCATION & TRAINING
Offer regular training sessions that educate employees about common attack vectors, social engineering tactics, and the importance of secure practices.
LEADERSHIP AND ROLE MODELING
Leaders within an organization must champion the security mindset by adhering to best practices and prioritizing security in decision-making.
INCIDENT RESPONSE PLANNING
Develop well-defined incident response plans that outline actions to be taken in case of a security breach. Regularly test and update these plans to ensure effectiveness.
AWARENESS CAMPAIGN
Engage employees through awareness campaigns highlighting real-world cyberattack scenarios, illustrating the potential consequences of lax security practices.